FORRESTER WAVE™
See why Red Canary is a leader with the highest possible score in nine criteria, including threat hunting and managed detection
INCIDENT RESPONSE & READINESS GUIDE
This guide arms security teams with the blueprint for a modern and effective incident response plan
THREAT DETECTION REPORT
Get the actionable insights you need to face the top threats, techniques, and trends in the evolving threat landscape
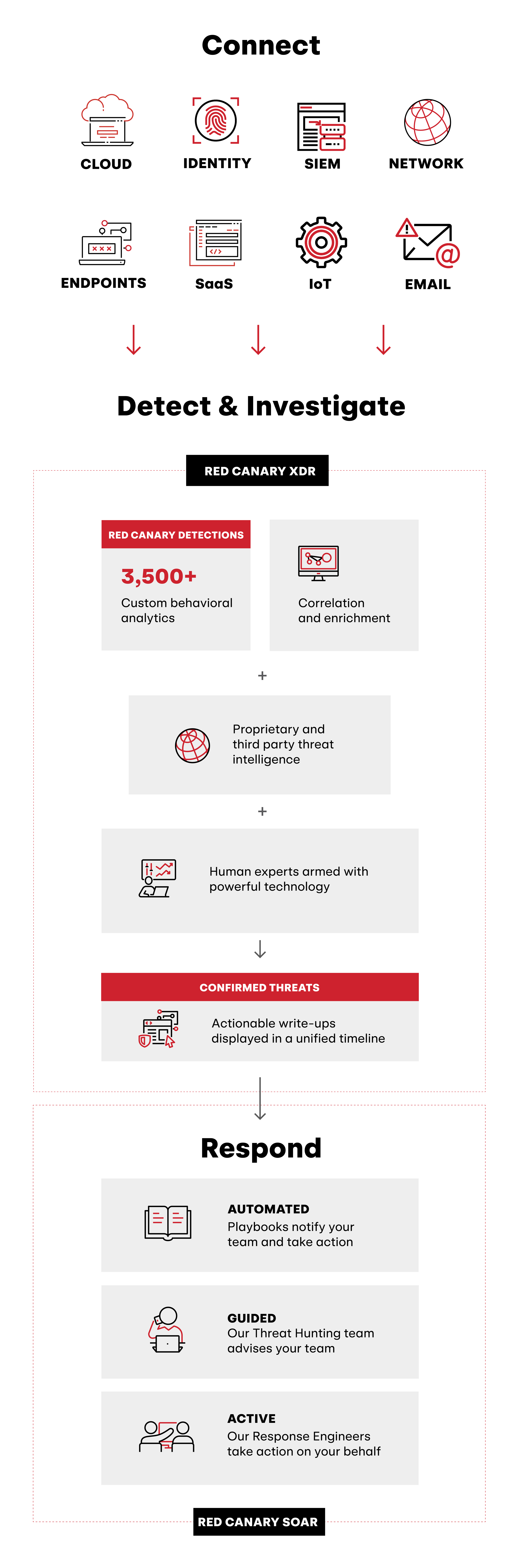
We deliver managed detection and response (MDR) across your enterprise
Trusted Detection & Response
Know that you’re prepared for modern threats, go beyond the alerts in your inbox, and automatically respond to and remediate the real threats.
Expert Led
Intelligence, investigation, and response from the experts who pioneered behavioral analytics, testing, and mapping to ATT&CK.
Cloud Native
We operationalize your security tools in minutes without complicated deployment, onboarding, or content creation programs.

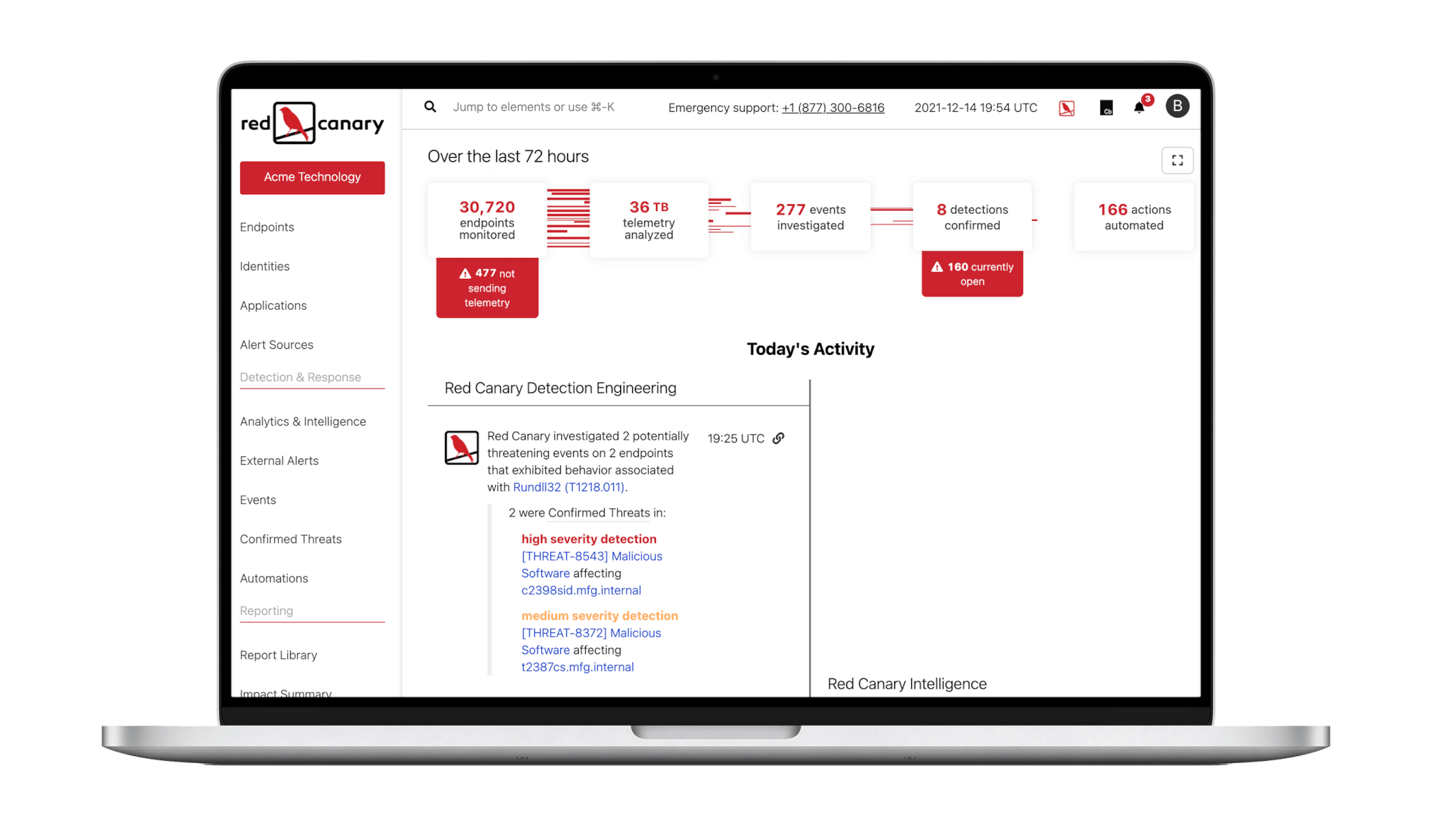
See the Red Canary Difference
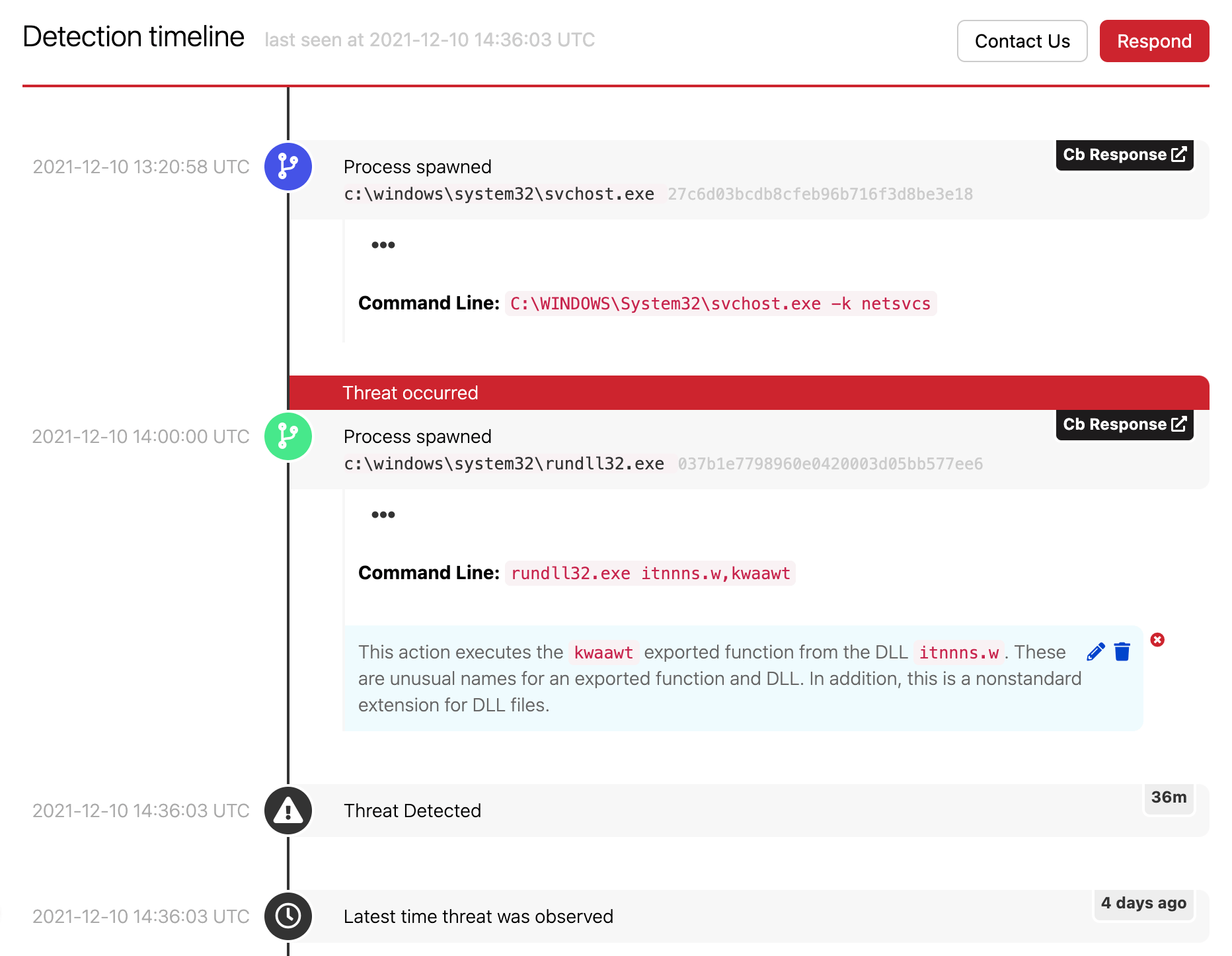
We hunt differently
We optimize for coverage and cast the broadest detection net possible with more analytics and security telemetry than anyone else.
3000+
Analytics
20000+
Detection Coverage Tests
1+
Petabytes of security telemetry per day
What others are saying
We’re here to improve the entire community
Even if you’re not ready to join the flock yet, we’re committed to educating and supporting every security team through open source, resources, and community programs.