For much of the cybersecurity industry, purchasing new products every few years is the status quo to “staying ahead” of adversaries. We’ve built moats, extra high castle walls with barbed wire, added sharks with laser beams to the water, fortified the castle door—yet somehow, something evil still creeps its way in.

And if you haven’t, check out this blog post on endpoint security vs network security for a deeper dive.
Living-off-the-land attacks are at their peak, and more than three-quarters of attacks use fileless malware. What comes next will define how we detect or prevent adversaries. As fast as security products are attempting to keep pace, those of us in the field should be asking ourselves: why are the products not yet ready? Why do we have to keep buying new things every two to three years to keep pace? How do we prepare our organizations today for the threats they’ll face tomorrow?
Moving from Reactive to Proactive
Investing in traditional infrastructure (firewalls, NAC, proxies, WAF, IDS/IPS, and so forth) is not going to solve the problem, especially for those who are defending global infrastructures with varying business operations. What if we change the way we think about this? A better approach may be to mix traditional security practices like antivirus with a more progressive agenda. Keep the idea of focusing on the “crown jewels” and begin to enhance how to protect the perimeter (mobile and on-premise) while taking a proactive approach to protecting employees.
In my previous “Security Architect Lessons” article, we discussed the pinwheel below, which is a visualization of the ongoing process you can implement to improve your security posture:
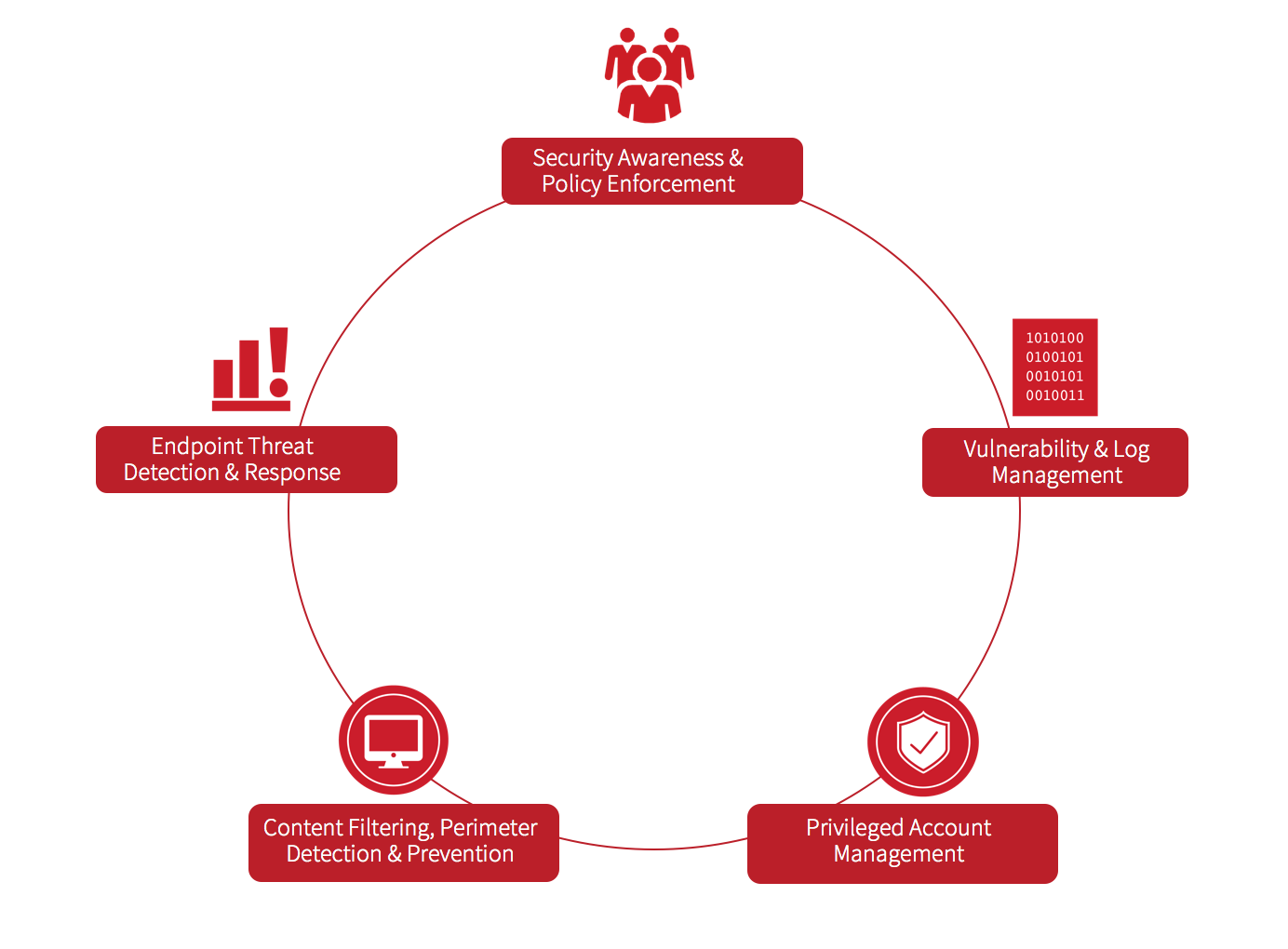
1: Security Awareness & Policy Enforcement
The idea of this is to focus on ensuring every employee across the business understands what policies are in place, where they are located, and how they are enforced. (We’ll dig deeper into enforcement later in this article.)
Every organization should have a plan to educate employees on phishing campaigns. If a technological control is in place, it should be tuned appropriately to inspect attachments and warn employees if an email is from an outsider (not the CxO). Actors will change tactics and return to them over time. Not as effective, but still used over the years, are password protected compressed files with the password in the body of the message. Not much out there today uses AI to pull that password from the message and decompress the zip.
This all sounds basic, right? Yet in the wild, we find that most organizations have not set up the basic policies. Make sure that applying and enforcing policies is on your radar. Monitor and update your policies with your legal counsel as you both see fit. Sometimes we need help; AuditScripts is a great tool to assist you with the basic policies and provide a way to audit against them.
2: Vulnerability and Log Management
If you don’t have a vulnerability management program today, you probably don’t know what is on your perimeter, or worse yet, what old software is lingering on endpoints. We won’t drill into the SANS CIS Critical Security Controls much here (inventory is just as important), but there is definitely overlap. Understand what level of risk is currently being accepted, clean up the critical and high risks, and begin working your way down to a more secure organization. Not everything can be patched, but knowing a vulnerability is there is 90% of the battle.
This is also the time to compare your servers/workstations to a baseline. The CIS baselines are a great standard with a plethora of related information readily available. Not everything has to be enabled, but a good understanding of where you are in regards to it is key. Take action based on criticality of the delta and what is not needed for enablement in your organization.
Whether you have a SIEM or not, consider storing your logs in a central place—not only for simplicity of management, but also to protect them from malicious intent. When a breach occurs, or if someone just asks a question, you should be able to go back in time and answer everything you need to know. So many times during an investigation, we run into a situation where logs are not properly retained and critical information about the incident is lost. It doesn’t have to be an expensive SIEM; it can be a protected central syslog server with limited access. Having your data somewhere is important no matter the size of your organization.
3: Privileged Account Management
Sounds easy, right? You may see and hear less about it, but we still have an account management problem. Overprivileged service accounts, users with local admin rights, global administrative accounts that aren’t properly secured, to name but a few. Some organizations may feel they’re too small to be hit by something that would consume a privileged account—until the day ransomware uses mimikatz to dump credentials from memory and begins to spread like wildfire. We need to have a better way.
Whether you’re using a central password vault, reducing exposure with proper group policy, or actually monitoring and alerting on account lockouts and abuse, this will continue to be a problem for every organization.
Here are a few things you can do:
- Assess your organization. How bad is it? How many accounts are domain administrator?
- Assess your system hardening practices. Do they align well with CIS guidelines? Or a big miss?
- Run a penetration test. Sometimes having your vulnerabilities exposed and abused is a great way for the organization to realize the importance of privileged accounts.
For those of you out there that have accounts under control, what have you done? Shout out to me (@M_haggis) on Twitter with your recommendations and steps taken.
4: Content Filtering/Perimeter Detection/Prevention
Depending on the organization, risk appetite, mobility, and openness, considering a cloud-based content filtering solution over on-premise hardware should be a main topic of discussion. Protecting employees while traveling or working from remote locations always seems to be a struggle. You either proxy all their data to the cloud, secure their DNS, backhaul to the corporate office across the country, or do nothing at all. Again, depending on the organization’s risk appetite and how we architect the system, a hybrid model of on-premise hardware and remote user protection is needed.
Most “next gen firewalls” (remember UTM?) offer the ability to protect on-premise and sometimes remote employees. Monitoring the logs in these appliances are usually eye-opening when we see certain departments reaching out to foreign destinations, or worse, submitting confidential information in the clear to a random site on the internet. The visibility and protection is worth every cent. If you are a cloud-built organization, consider placing something in front of cloud systems to monitor and protect. Keeping an eye on your assets is an important part of having good cyber hygiene and why we recommend focusing on the endpoint instead of the four walls with a firewall.
5: Endpoint Threat Detection and Response
Every day an organization realizes their endpoints are performing actions they don’t know about. Bad guys are running PowerShell, WMIC, using SNMP traps, submitting data to foreign IP space, and everything else we hear about in the media. What is the best thing we can do?
First, question your current security stack. If all the items described are common areas you have no visibility in today, it’s probably worth looking into an endpoint detection and response (EDR) product. If you are still an antivirus believer, but sometimes wonder if malware remnants or living-off-the-land attacks can bypass you, an EDR product will help you know what is happening on your endpoints day and night. It can help with everything from taking inventory of software and assets to understanding what processes are executing. The use cases are endless.
Dig Deeper: How to Use EDR to Understand Your Environment
Closing
In information security, following the basics can sound unsexy compared to all the whizbang unicorn pixie dust products that promise to solve our problems. Ultimately, we have to determine what best fills the areas of need for our individual organizations and move forward with that. Having a proper long-term security strategy in place really helps to set the tone internally for where your program will go. Focus on what can affect your organization the most and begin to roll that plan out. It doesn’t happen overnight and it will take time and perseverance. But the results will be worth it!
I hope this was informative and opens a discussion between you and your organization on making informed security decisions. If you have any questions or tips that helped you, hit me up on Twitter.