At Red Canary, we’re always looking to simplify our customers’ security operations.
Responding to the confirmed threats you receive from Red Canary is simple: isolate the endpoint, craft a response plan, and execute. Ready? Start the clock.
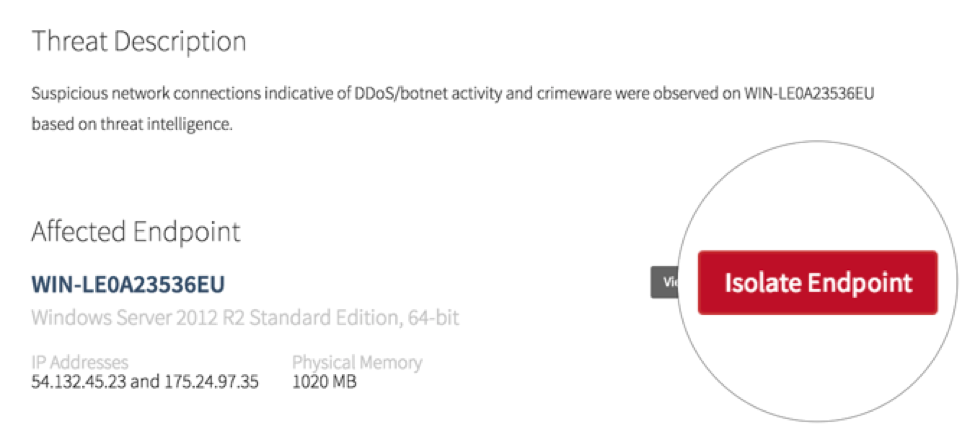
Your Red Canary detections include the buttons: “Isolate Endpoint” and “Respond.”
Isolating the endpoint disables all network communication from the endpoint to anywhere except the Carbon Black server. Fair warning: with great power comes great responseability to isolate your domain controller, so be careful. Once you’ve clicked Isolate, you have instantaneously quarantined an endpoint and stopped the bleeding whether you and the endpoint are 5 feet or 5,000 miles apart.
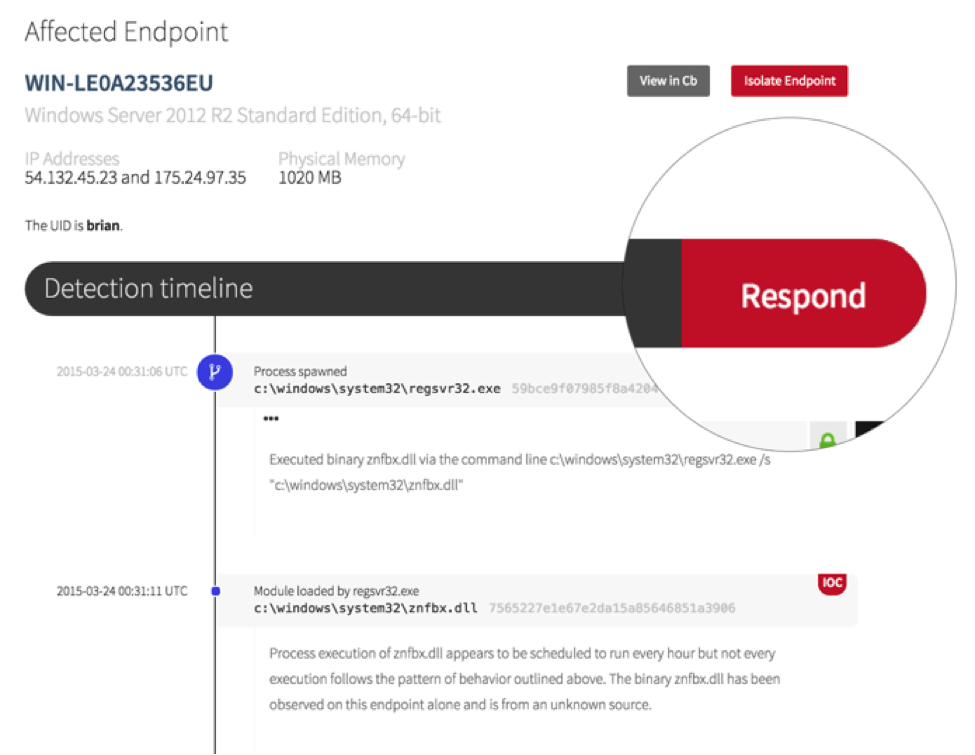
Now we need to respond to the threat by clicking the big ‘ol Respond button.
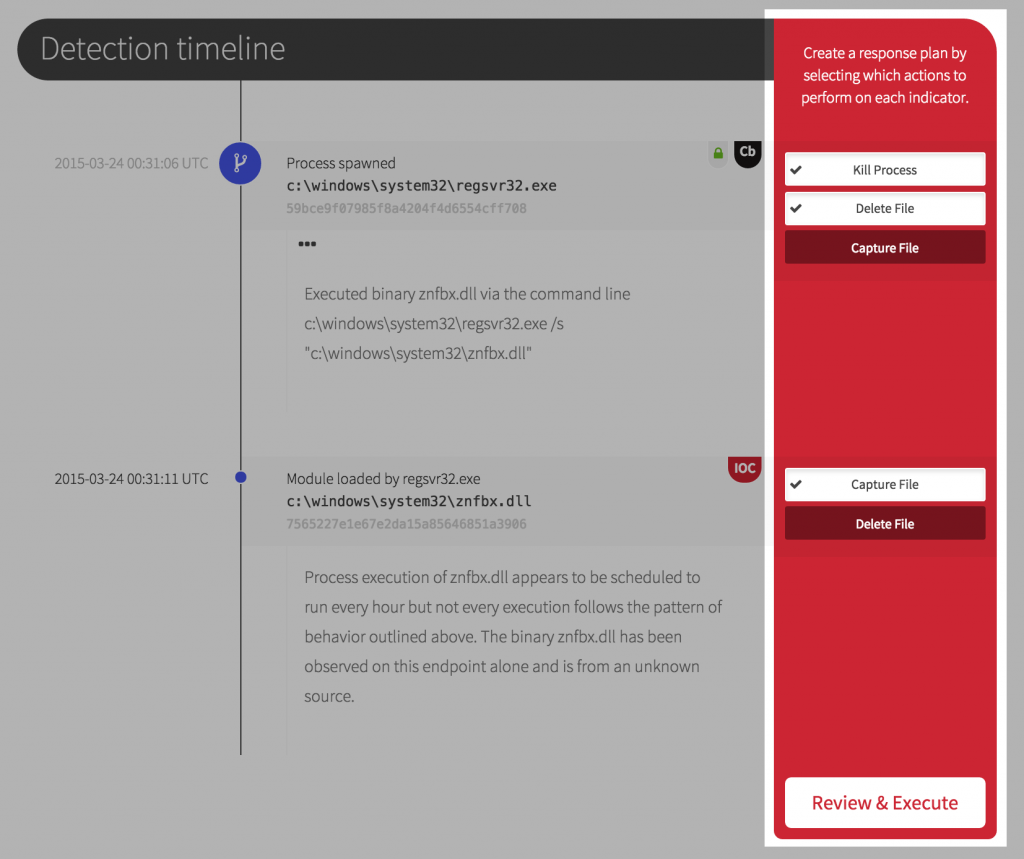
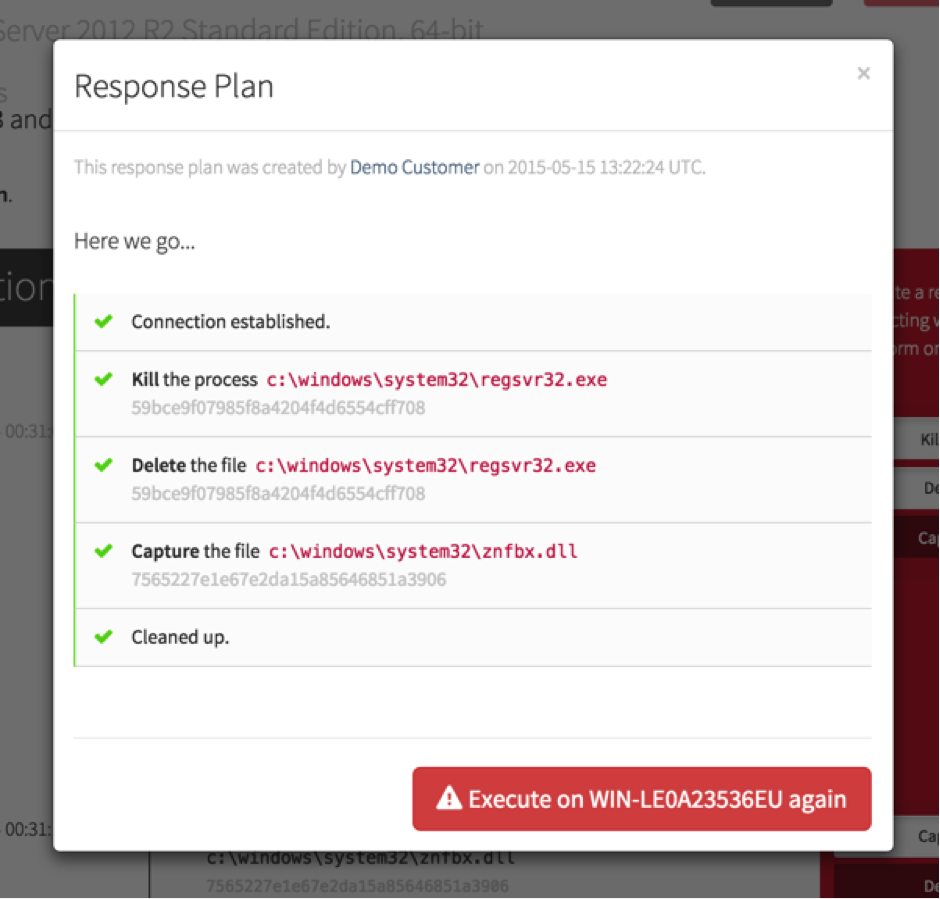
For every relevant bit of endpoint activity or indicator of compromise in the timeline, you have associated actions to assist your response. Kill a process. Delete a file. Even capture a binary for later analysis.
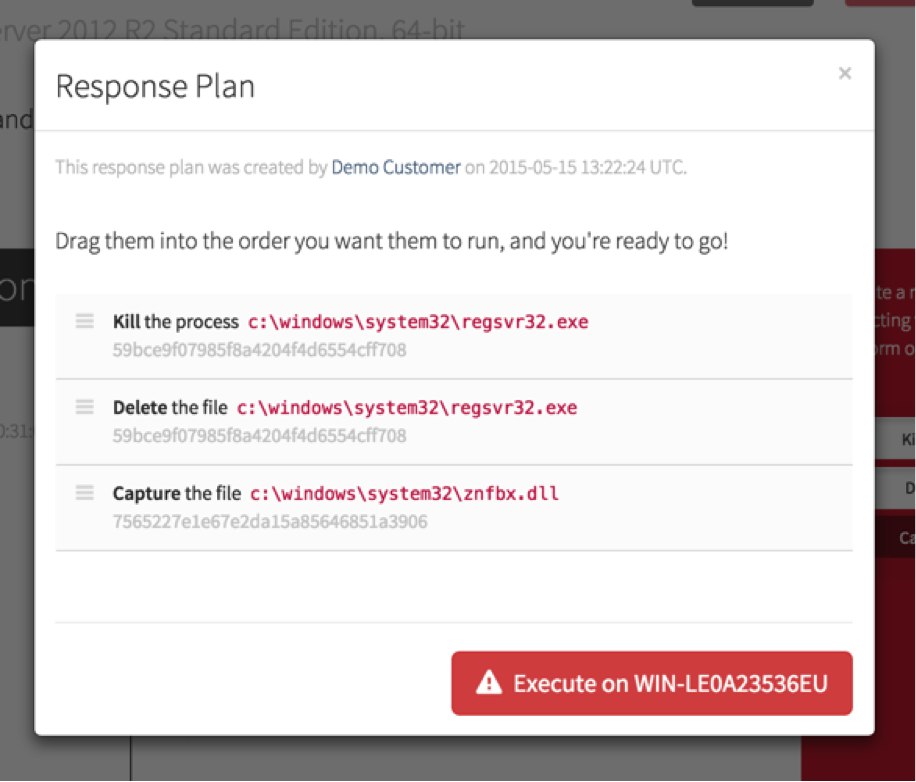
Once you have selected the actions that you would like included in your response plan, review and reorder the elements as necessary (you should probably capture a file for further analysis before you delete it) and then execute the plan.
At this point, Red Canary connects to the endpoint, executes the actions, and reports back to tells you what out of your response plan succeeded and what failed. The results of the response plan are recorded so you can avoid cleaning things multiple times and audit who has executed response activities on your endpoints.
As you can see, responding to threats in your organization doesn’t need to be overly complex. We understand the battle security teams are in against attackers and insider threats and how every improvement in threat detection and response can be the difference between a successful attack and a foiled breach. We hope you’ll join us and let Red Canary help you defend your endpoints.