One hallmark for many malware events is the regular periodic behavior they present when rallying for and checking in with their command and control servers. The check-in interval can be a very useful metadata point in hunting an adversary. However, the constant state of change that attackers can use for their own infrastructure makes this a challenge with traditional methods.
Typical Indicators of Compromise (IOCs) such as IP addresses and host/domain names have a short shelf life due to methodologies such as fast flux DNS and domain name generation algorithms. Malware authors are constantly improving their methodologies and we must improve in kind. The most effective place to look for evidence of techniques and behaviors is on the end. In some cases, this includes identifying periodic actions on the endpoint that don’t cause any network activity at all.
A recent detection highlights one of the advantages of using process-centric information to detect threats rather than just traditional IOCs.
In this case, Red Canary analysts immediately honed in on an unusual command line argument including the string “###client###“. Also note that our enrichment routines identified that the domain in use was recently registered–a frequent indicator of attacker activity.
At this point, we’ll take a look at how our analysts determined this was malware exhibiting periodic behavior related to command and control activity. To demonstrate this, we’ll show some screenshots from the corresponding event in the Bit9+Carbon Black interface.
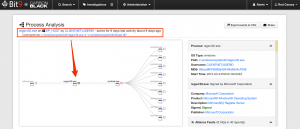
First, note the full command line used to launch “regsvr32.exe“. This command line registers the “fkwph.dll” file (which is not a standard component of the Windows operating system) to the registry, and the “/s” switch performs the task without triggering any dialog boxes to users that may be logged into the system at the time. The corresponding execution event is depicted below, in the tree hierarchy.
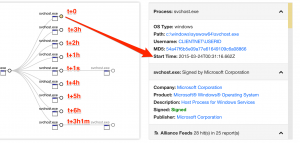
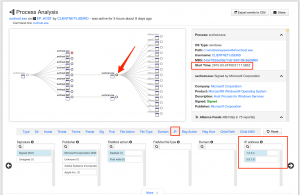
The timing of each child “svchost.exe” process is what helped lead the Red Canary analysts to classify the event as malicious. As shown in the first screenshot below, the first event starts at 12:31:16 UTC, with processes starting at precise one hour increments – an obvious periodic interval. Two of these processes spawned additional child “svchost.exe” processes executed within one minute of the parent. In the second screenshot, you can see the second child process, which opened network sockets to each of the two IP addresses listed in the detection notification.
Without the richness of context that the endpoint provides, the minimal network profile the malware presented would have almost certainly been lost in the deluge of gigabits of network traffic. However, with Red Canary’s analysis and detailed detection notification message, the customer was able to enact remediation procedures to mitigate the threat realized just hours after it first occurred.