It’s been nearly nine months since we launched Atomic Red Team and we’ve been blown away by the tremendous response from the community. It’s exciting to see so many teams testing their security controls and getting a better understanding of what they can and cannot detect.
We initially created Atomic Red Team to help security teams (including our own) test detection coverage against the best adversary tactic/technique taxonomy, MITRE ATT&CK™. The project was founded on these core beliefs:
- Testing coverage is fundamental to improving security outcomes.
- Testing should be fast and easy.
- Defenders need to keep learning how adversaries are operating.
The response from the community has been overwhelming and has demonstrated that there was a massive need for this type of project. After dozens of contributions, calls, and conference talks about Atomic Red Team, we are using the feedback and ideas we’ve heard to guide the next chapter.
Watch the latest on-demand webcast, Automating Atomic Red Team, to hear from the research team and Blake Strom, co-creator of MITRE ATT&CK™
What’s Next for Atomic Red Team
We’re doubling down on our commitment to helping every security team test their controls with atomic tests. As we look to the future, our goals are to:
- Keep Atomic Red Team approachable and easy to use for humans and machines alike.
- Become the clearinghouse and repository for mechanisms to exercise adversary techniques.
- Provide great documentation that can help us all learn more about adversary techniques and how to simulate them.
- Be a foundational community resource that is well maintained and inviting to all.
We’ve learned a lot about how to support a great community project from many of the open source projects we use and support, most recently in work with the osquery community. Lasting projects need an active community of supporters, a core group of maintainers, and infrastructure thats supports collaboration, learning, and contribution.
With that in mind, we’re excited to announce five new developments.
1: New Slack workspace
New users and new contributors often have questions about how to exercise a specific technique or where they should start contributing. Slack workspaces are a great way to interact with others using the project and answer those questions. Our core maintainers will be active in Slack and hope you will be as well. Get an invite at slack.atomicredteam.io. (Note that your email address won’t be used for any purpose beyond extending this invitation)
2: Structured, machine-readable core
We recently wrapped up the conversion of Atomic Red Team content from pure Markdown to YAML. YAML is a structured, human friendly language that makes it easy to describe structured content, in our case, the “atomic tests” associated with an ATT&CK technique.
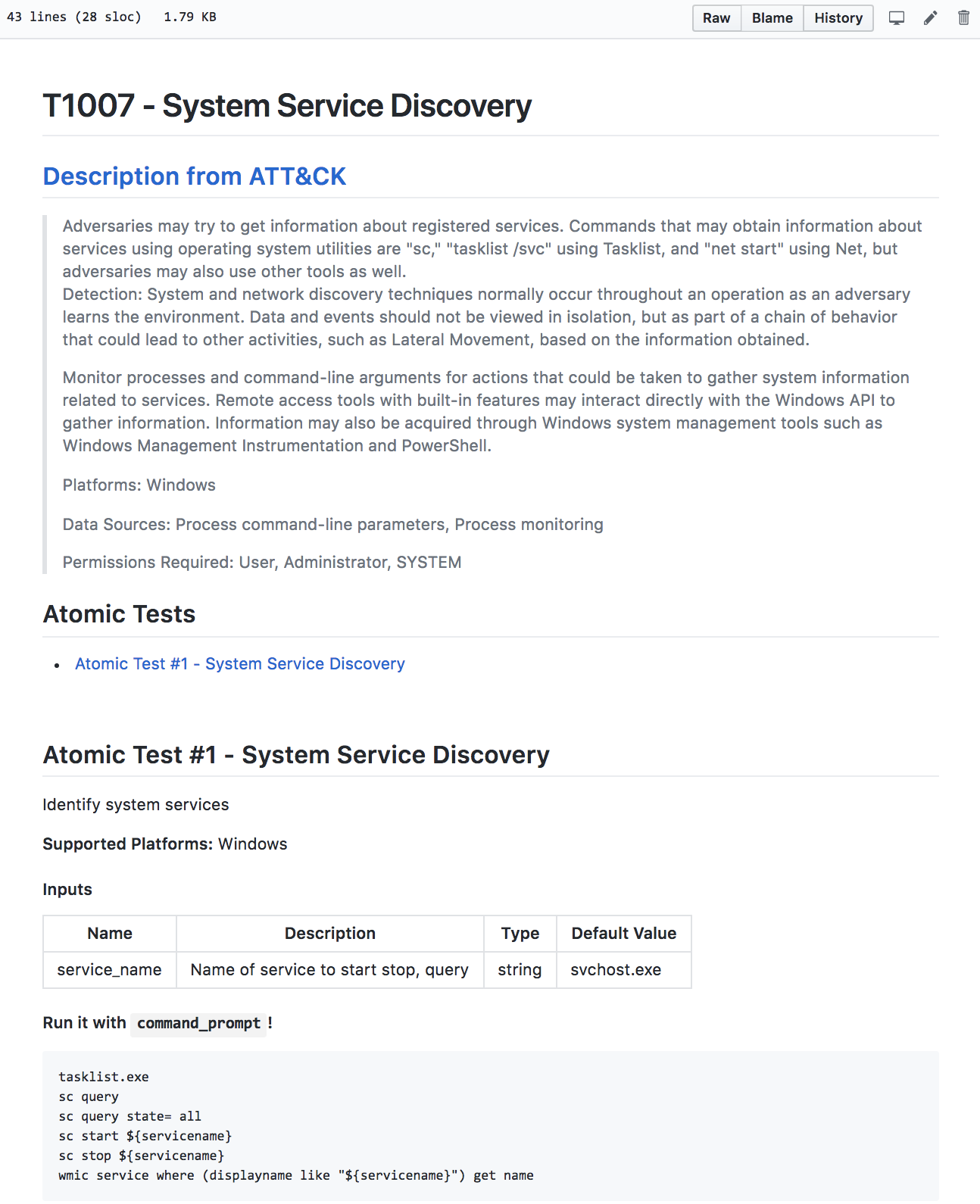
Each Atomic Test has two bits of key information: metadata about the test and the definition of how to execute the test. Test metadata includes name, description, and the target platforms and operating systems. This metadata is key to the great documentation Atomic Red Team provides and also allows us to generate the platform specific ATT&CK + Atomic Red Team matrices (Windows, macOS, Linux).
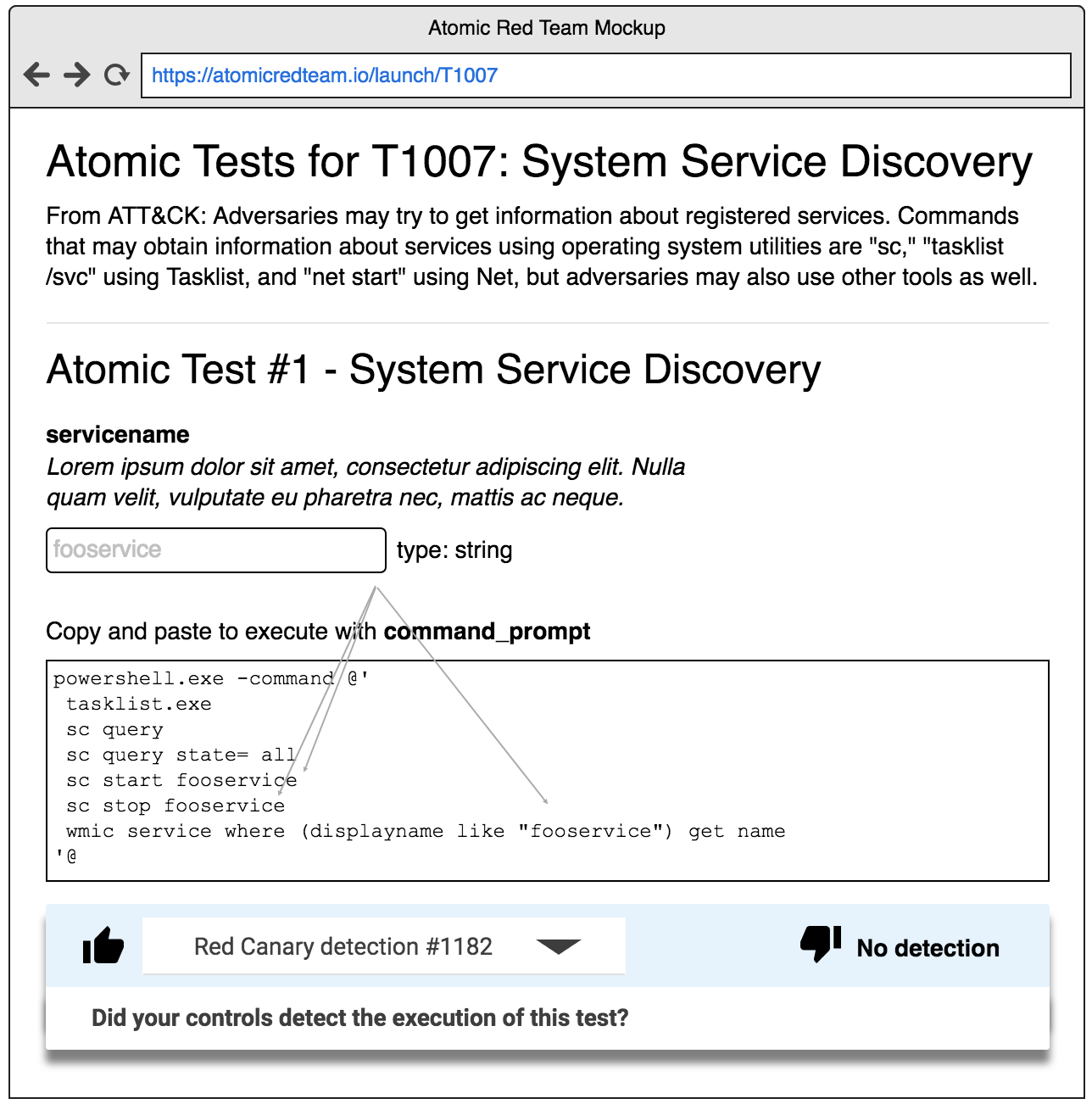
Here’s what that metadata looks like for the T1007 tests:
- What system or tool do I use to run it? (Think Windows command prompt, bash, PowerShell, manual steps, etc.)
- What arguments do I need to provide that are specific to my environment? (Think target hostnames, usernames, payload locations, etc.)
- What command(s) do I run?
The combination of these three items gives us the complete information needed to run the test. They also are the foundation for any automation framework to prompt you for this information, automatically execute the test, and store the results.
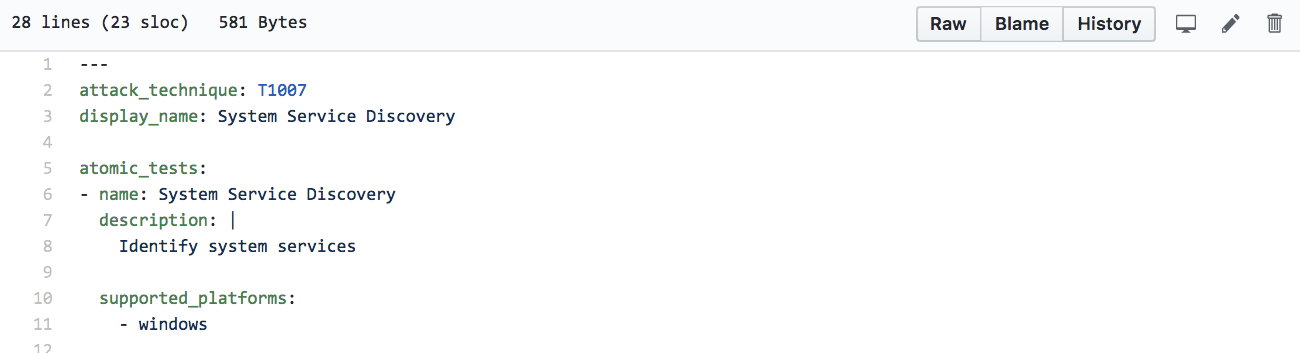
Here’s what the arguments and execution definition for T1007 look like:
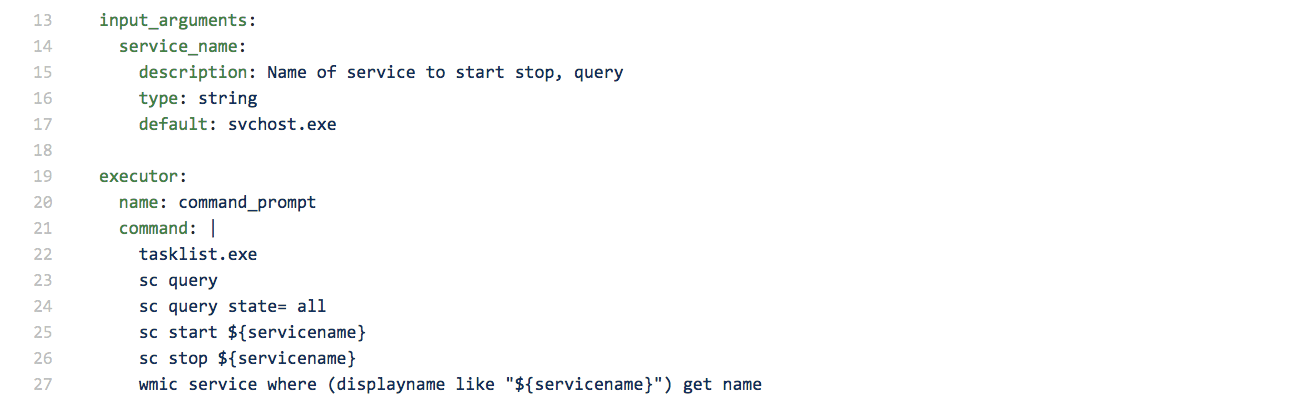
3: Markdown docs include ATT&CK context
A core principle of Atomic Red Team is ease of use, and we all love the Markdown documents. Markdown is now automatically generated from the core YAML files on every commit, and pulls in technique descriptions and other context from ATT&CK’s Cyber Threat Intelligence repository.
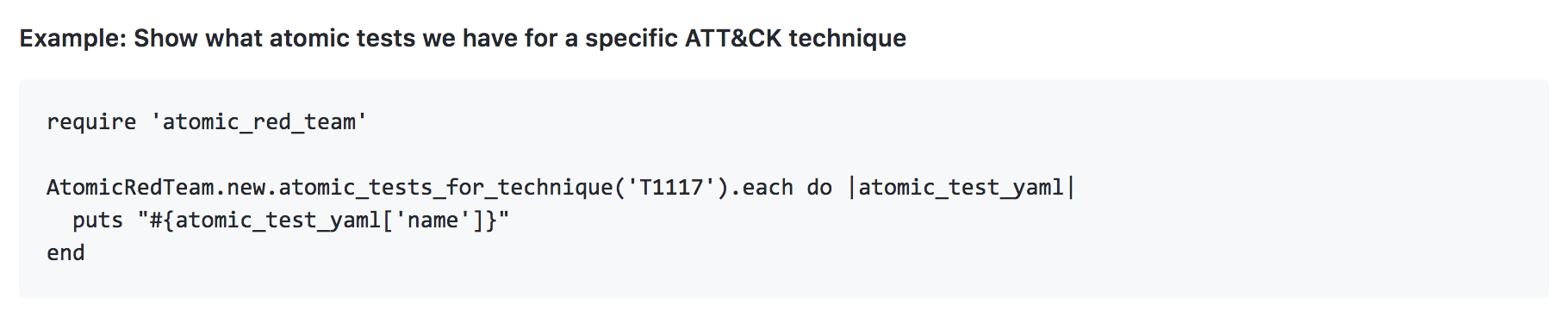
4: APIs for automation
For Ruby users, the Atomic Red Team Github repository is now a Rubygem and can be loaded into your project in seconds. APIs are provided for accessing Atomic Red Team tests as well as the underlying ATT&CK context so you can simply iterate over and begin automating the execution of tests.
5: New GitHub Pages site: atomicredteam.io
New users can get started testing and browse guides about different use cases at atomicredteam.io. We’ve learned that many of you are using Atomic Red Team for various purposes. Some of these ideas have included:
- Testing your production security controls
- Testing the coverage of a product during a proof of concept
- Testing your analysis team and processes
The microsite content lives in the repository’s “docs” directory and can be updated like any Atomic Red Team content via Pull Requests.
Ways to Contribute and Help the Community Grow
We’re extremely excited for this next chapter of Atomic Red Team helping security teams understand their controls and how adversaries operate. This project has already made a meaningful difference to dozens of security teams and hundreds of researchers. As a community, we can make that thousands.
Here’s how you can can get involved today:
Contribute a new atomic test!
You can see from the master list of tests that we’re just getting started covering the complete ATT&CK matrix. A great way to contribute is to pick a technique you want to learn more about, read the ATT&CK docs, do some testing, and document that test following the Contributing guide.
Join us in Slack.
Bring your questions and ideas! We want this to be an interactive community that continues to help us understand how we can make Atomic Red Team as useful as possible for real-world security teams. Get an invite at slack.atomicredteam.io. (Note that your email address won’t be used for any purpose beyond extending this invitation)
Check out our resources.
We regularly hold training sessions and write articles to educate the community on what’s new. Browse our library of resources at redcanary.com/atomic-red-team.