THE RED CANARY DIFFERENCE
There’s MDR. Then there’s Red Canary.
A true security partner dedicated to improving your outcomes—integrating with your existing tools, backed by 24×7 expert support, and focused on stopping threats before they can do harm.
See The Red Canary Difference- Unmatched threat detection
- Actionable intelligence
- Expert-driven response
- Seamless integration
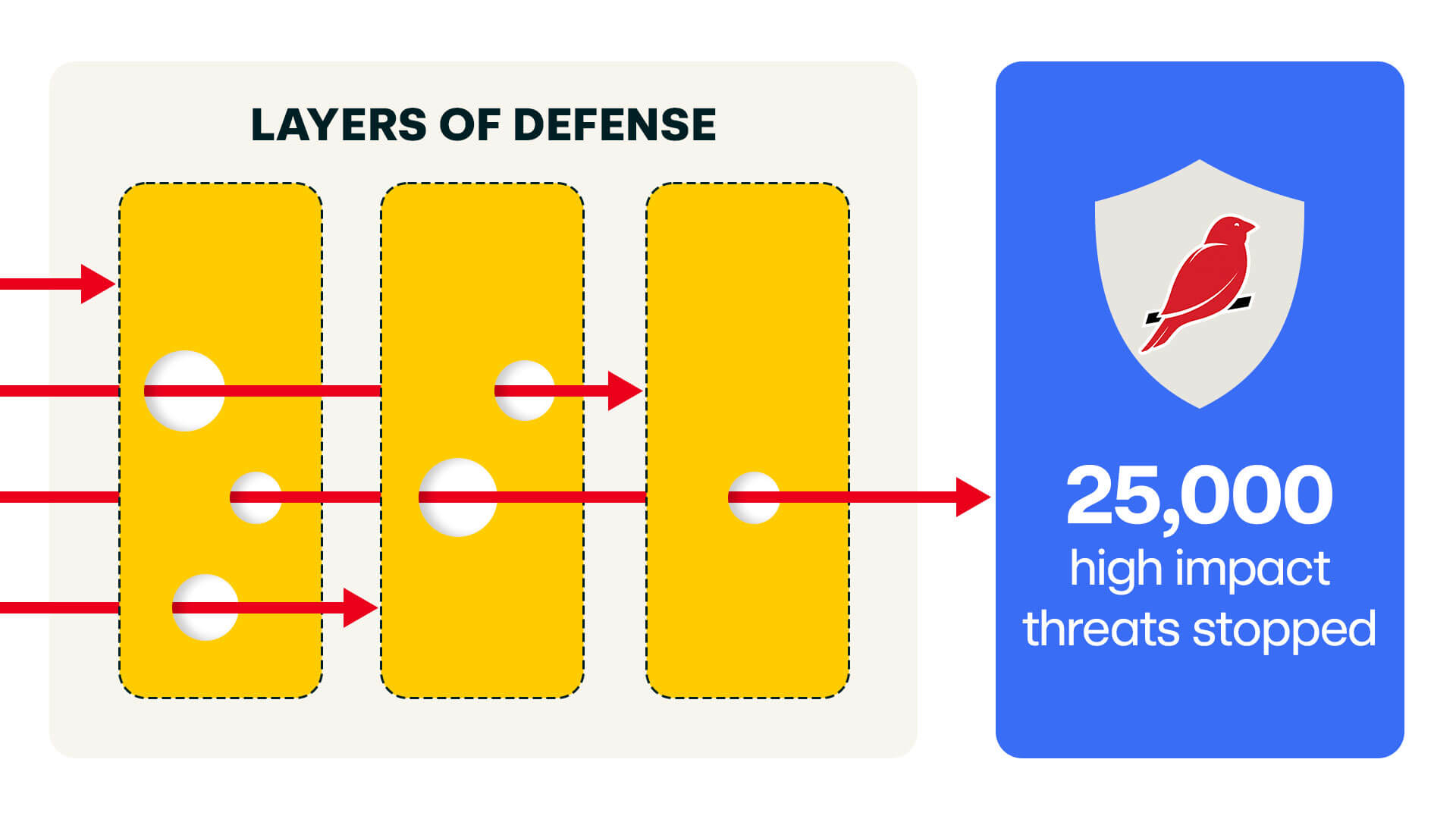
Find 4x more threats. Miss nothing.
Go beyond legacy alerts to find what your other security tools miss. Our unique combination of detection-as-code detection engineering, proactive threat hunting, and agentic AI uncovers critical threats deep within your environment before they cause harm.
Get intelligence you can act on—fast.
Generic threat feeds often create more confusion than clarity. Our renowned in-house intelligence team provides tactical insights tailored to your unique environment, helping you understand the adversaries you face, their specific tactics, and how to stop them.
Shut down attacks 10x faster.
A slow response gives adversaries the advantage. We help you slash your mean time to respond (MTTR) by detecting threats early, investigating with precision, and enabling rapid expert-led and automated containment.
Get more value from your existing security stack.
Red Canary continuously analyzes your critical data to detect and stop more threats, with the option to add our Security Data Lake for cost-effective compliance and investigation.
YOUR TOP SECURITY CHALLENGES, SOLVED
Every security team has one goal:
Don’t get breached.
With Red Canary’s managed detection and response (MDR), you get everything you need to detect critical threats across your endpoints, identities, and cloud; respond with confidence; and understand your true risk—all backed by our 24×7 team of experts.
Focus on stopping real threats, not chasing alerts. Our blend of human expertise and agentic AI delivers confirmed detections with the full context you need to act quickly and decisively.
Retain top talent by offloading detection, investigation, and response to our experts, freeing your analysts to focus on high-impact work and prove your program’s value.
Make defensible decisions, communicate to the board, and measurably lower your cyber risk with trusted, executive-level visibility and high-fidelity threat detection.
“A 24×7 extension of my team”—that’s what true peace of mind feels like.
Hunt down hidden threats, automate investigations, and get intel you can act on—all from a trusted team of experts acting as an extension of your own.
Elite operators
Get peace of mind with 24/7 pro coverage from detection to remediation.
Expert AI agents
Reduce noise, respond faster, and unlock expert analysis for every threat.
Customer experience pros
Gain a strategic partner dedicated to your long-term security success.
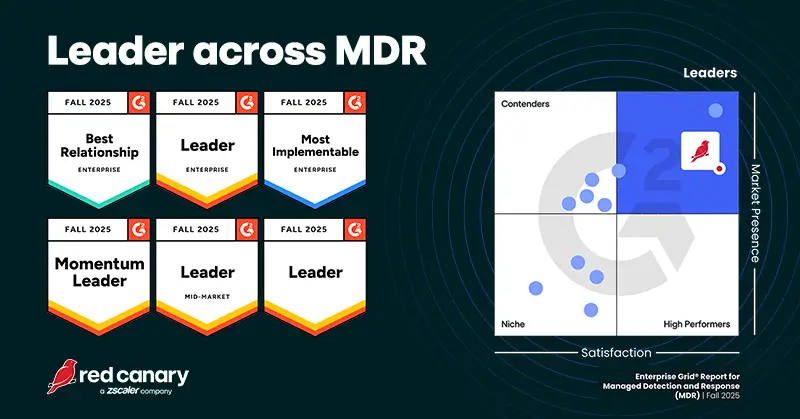
Analysts call us a leader. Customers call us a partner.
With a 99% customer satisfaction score and over a decade of experience, see why thousands of organizations have put their trust in our team.

“Red Canary stands out for customers looking for a provider with superior detection and response capabilities that remains flexible to the unique needs of their organization.”
The Forrester Wave™: Managed Detection And Response Services, Q1 2025 Learn More

“Red Canary caught something that we would have otherwise missed. There’s a capability gap in current security solutions, and only one of our tools is capable of filling that gap. Red Canary is the only one I know of that could have detected the suspicious activity we saw.”
CIRT TEAM MEMBER, DUPONT Learn More

“Red Canary acts as a filter for us: they bubble up the most pressing things to the top, and it’s very easy to collaborate with them within their portal. We get the most pressing alerts passed to our response team, and they get actioned first.”
DAVE COUGHANOUR, CISO, ANSYS Learn More

“With the steps Red Canary took after detection, we felt safe almost immediately. We were back to normal that morning. They were following up with us all day and even proposed follow-up items to make us safer going forward. It was an awesome experience.”